SOAR Program: Incident Response Automation and Orchestration Explained

What is a SOAR Program?
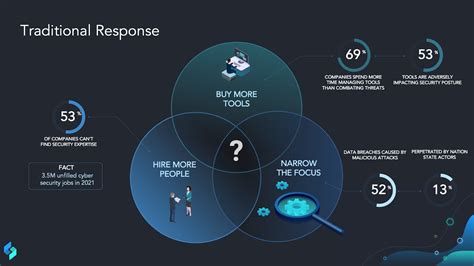
A Security Orchestration, Automation, and Response (SOAR) program is a software solution designed to help organizations manage and respond to security incidents more efficiently. It automates and streamlines the incident response process, making it faster and more effective. A SOAR program integrates with various security tools and systems, such as security information and event management (SIEM) systems, threat intelligence platforms, and security orchestration platforms.
Key Components of a SOAR Program

A SOAR program typically consists of three main components:
- Security Orchestration: This involves integrating various security tools and systems to create a cohesive and automated incident response process.
- Automation: This component automates repetitive and mundane tasks, freeing up security analysts to focus on more complex and high-value tasks.
- Response: This component involves the actual response to security incidents, including containment, eradication, recovery, and post-incident activities.
Benefits of a SOAR Program

Implementing a SOAR program can bring numerous benefits to an organization, including:
- Improved Incident Response: A SOAR program automates and streamlines the incident response process, making it faster and more effective.
- Increased Efficiency: By automating repetitive tasks, security analysts can focus on more complex and high-value tasks.
- Enhanced Collaboration: A SOAR program provides a centralized platform for security teams to collaborate and respond to incidents.
- Better Decision-Making: A SOAR program provides real-time data and analytics, enabling security teams to make better decisions.
- Reduced Costs: A SOAR program can help reduce costs by automating tasks, reducing the need for manual intervention, and improving incident response times.
SOAR Program Workflow
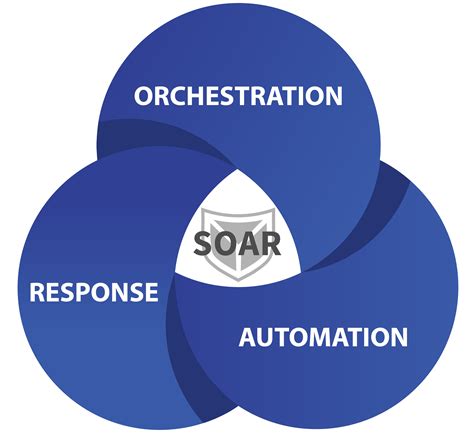
A typical SOAR program workflow consists of the following stages:
- Threat Detection: The SOAR program receives threat intelligence from various sources, such as SIEM systems, threat intelligence platforms, and security orchestration platforms.
- Incident Creation: The SOAR program creates an incident based on the threat intelligence received.
- Automated Enrichment: The SOAR program automatically enriches the incident with relevant data, such as threat intelligence, network logs, and system data.
- Analysis and Triage: The SOAR program analyzes the incident and determines the best course of action.
- Automated Response: The SOAR program automates the response to the incident, including containment, eradication, and recovery.
- Post-Incident Activities: The SOAR program performs post-incident activities, such as reporting, documentation, and lessons learned.
Implementation Considerations

Implementing a SOAR program requires careful consideration of the following factors:
- Integration with Existing Tools: The SOAR program should integrate with existing security tools and systems.
- Automation and Orchestration: The SOAR program should automate and orchestrate incident response processes.
- Scalability and Flexibility: The SOAR program should be scalable and flexible to accommodate changing security needs.
- User Experience: The SOAR program should provide a user-friendly interface for security analysts.
📝 Note: Implementing a SOAR program requires careful planning and consideration of the organization's specific security needs and requirements.
Best Practices for Implementing a SOAR Program

Here are some best practices for implementing a SOAR program:
- Start Small: Start with a small pilot project to test the SOAR program and identify areas for improvement.
- Define Clear Goals and Objectives: Define clear goals and objectives for the SOAR program.
- Establish a Governance Framework: Establish a governance framework to ensure the SOAR program is aligned with organizational policies and procedures.
- Provide Training and Support: Provide training and support for security analysts using the SOAR program.
- Continuously Monitor and Evaluate: Continuously monitor and evaluate the SOAR program to ensure it is meeting its intended goals and objectives.
📝 Note: Implementing a SOAR program requires a structured approach to ensure its success and effectiveness.
Common Challenges and Limitations

Implementing a SOAR program can present several challenges and limitations, including:
- Integration with Existing Tools: Integrating the SOAR program with existing security tools and systems can be challenging.
- Data Quality and Standardization: Ensuring data quality and standardization can be a challenge.
- Automation and Orchestration: Automating and orchestrating incident response processes can be complex.
- Scalability and Flexibility: Ensuring the SOAR program is scalable and flexible can be a challenge.
- User Adoption: Encouraging user adoption and buy-in can be a challenge.
📝 Note: Addressing these challenges and limitations requires careful planning and consideration of the organization's specific security needs and requirements.
A well-planned and implemented SOAR program can significantly improve an organization’s incident response capabilities, reduce costs, and enhance overall security posture.
What is a SOAR program?

+
A Security Orchestration, Automation, and Response (SOAR) program is a software solution designed to help organizations manage and respond to security incidents more efficiently.
What are the key components of a SOAR program?

+
The key components of a SOAR program are security orchestration, automation, and response.
What are the benefits of a SOAR program?
+
The benefits of a SOAR program include improved incident response, increased efficiency, enhanced collaboration, better decision-making, and reduced costs.



